
XDR + CSIRT + 24/7 SOC
Your BENELUX Tactical SecOps Partner
All your operational security needs covered by your local IT Security Partner.
Contact usCurrently under attack ?!
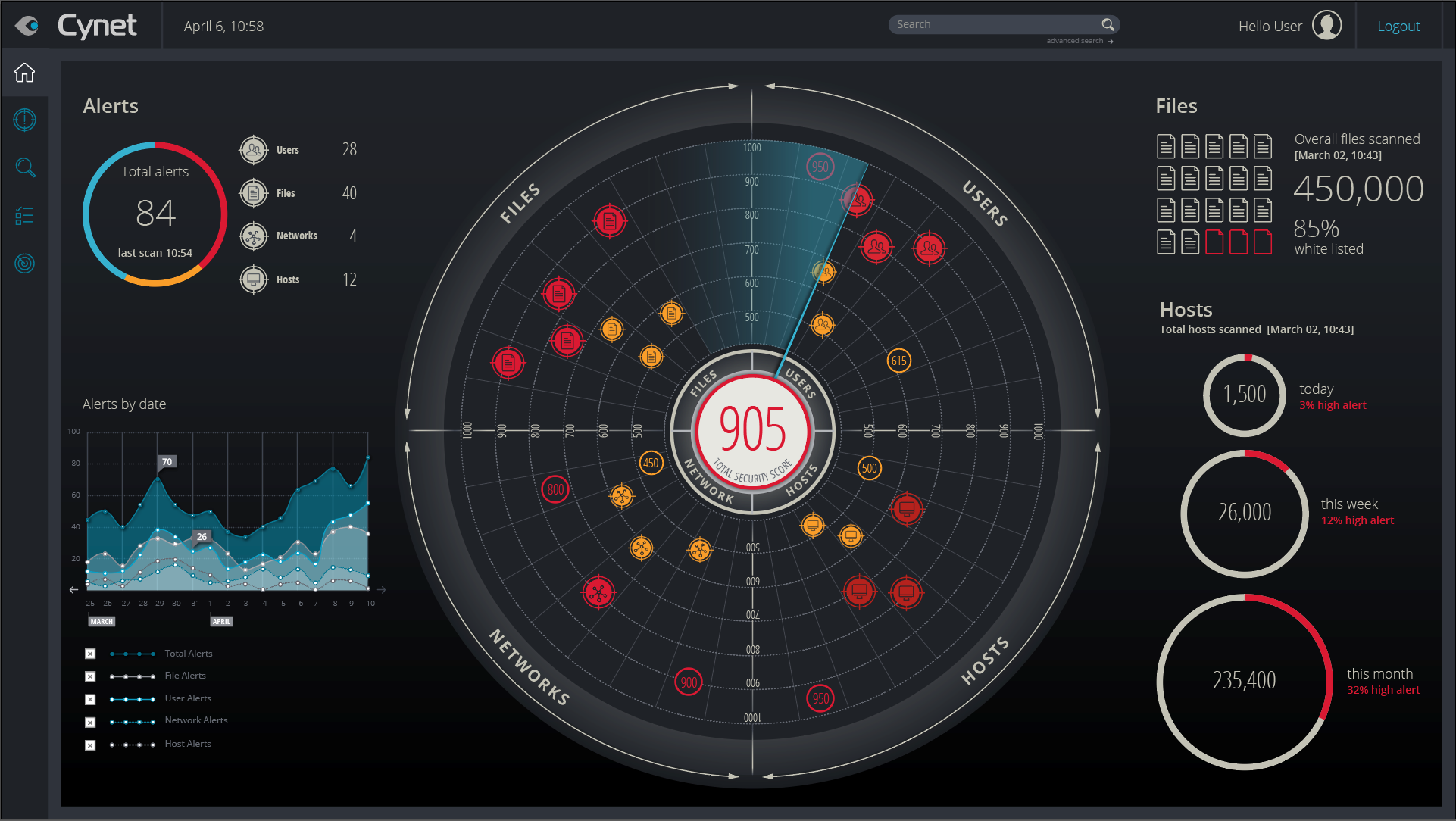
Prevention and Detection
Advanced endpoint detection techniques to prevent and detect both known and unknown threats across your environment.

Full XDR Capabilities
Full visibility across endpoint, network and users, along with deception technology, to detect stealthy (and otherwise undetectable) attacks.
XDR Prevention and Detection
Defend against a myriad of attack vectors, utilizing the capabilities of the following security technologies:
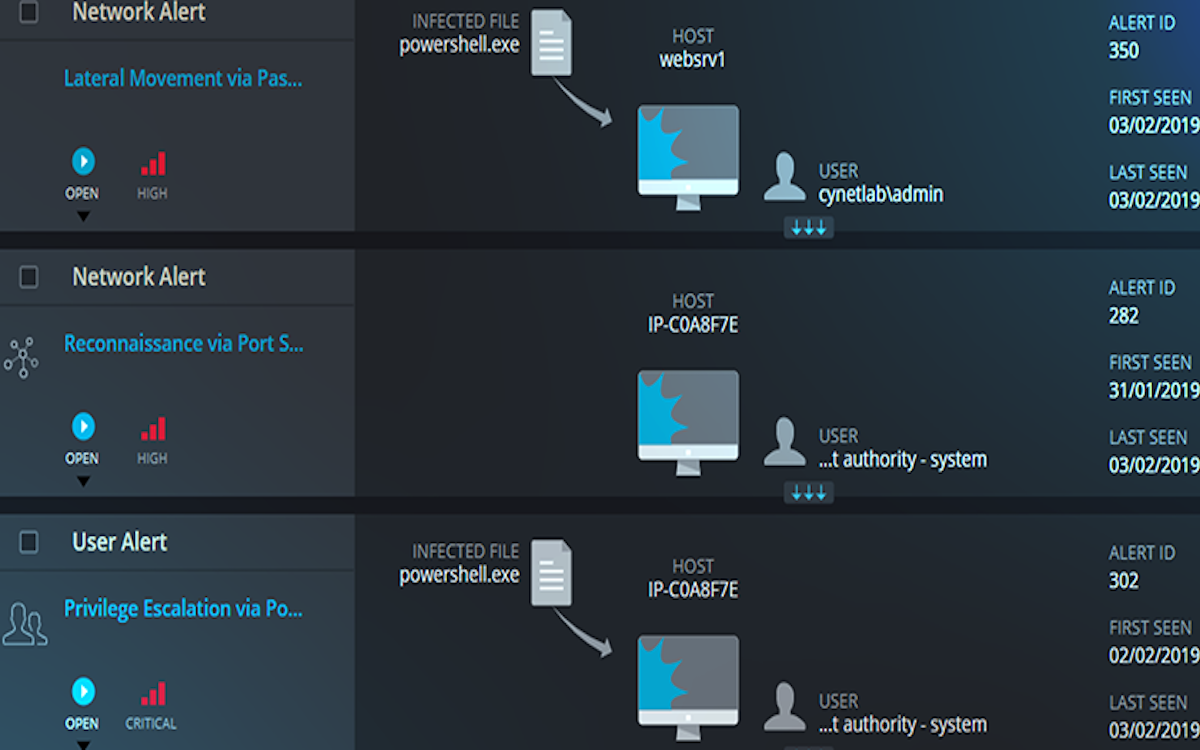
Manual and Automated Response
Remediations of infected hosts, malicious files, compromised user accounts and attacker-controlled traffic.

24/7 MDR Services
Leading expert threat analysts and security researchers at your service 24h/24 7d/7.
